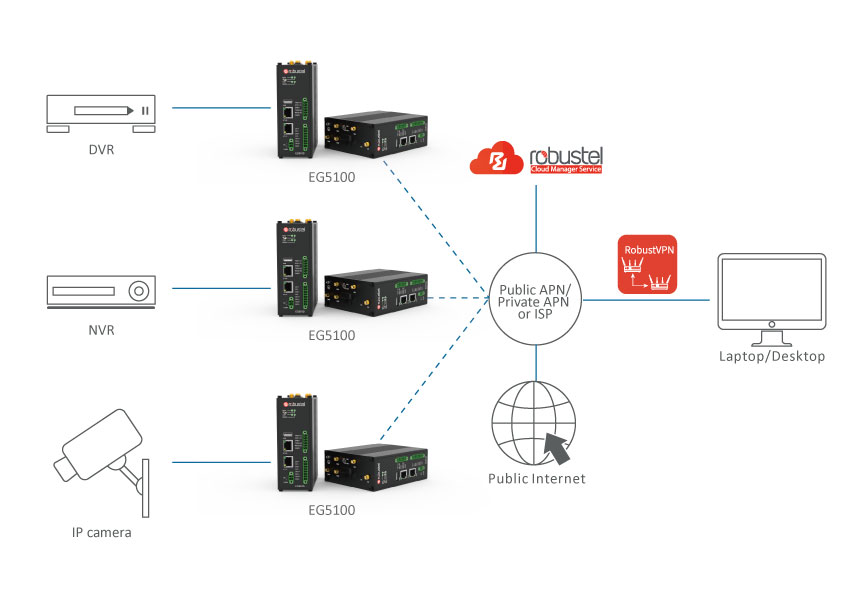
Uncovering Trickbot's use of IoT devices in command-and-control infrastructure | Microsoft Security Blog

Amazon.com: LBDCIOT Data Only SIM Card for IoT Devices,180 Days 12GB Internet Data Compatible with AT&T and T-Mobile Networks for USA Only : Cell Phones & Accessories